Anatomy of a hospital cybersecurity attack
September 12, 2018
By Mike Kijewski
Security is the collective responsibility of all players in a healthcare delivery organization (HDO), from vendors and third parties to threat intelligence-sharing platforms.
What makes healthcare, and particularly hospitals, a popular target?
● Highly valuable data – the volume of personal health information and financial details stored, combined with their sensitive nature, as nearly all of the data is governed by government regulations
● Lack of IT investment and training – healthcare is noted to have the lowest confidence in endpoint security, with 72 percent of participants feeling they are not up to the job of protecting endpoints from exploitation
● Highly connected systems – the scale of the IT infrastructure, overlapping systems, bluetooth/wireless connected devices and data constantly in transit increases the size of the threat landscape
According to the Ponemon Institute, this is the seventh year of healthcare data breaches costing the most, estimated at more than 2.5 times the cost of similar attacks in other industries.
To best defend against increasingly sophisticated cyber threats, we assess the threat landscape of an HDO, typical threats and better practices in preparing for a breach.
Assuming the reality of an HDO includes overlapping systems, lingering legacy systems and connected medical devices, it is easy to conclude HDOs and medical device vendors are faced with securing a complicated array of endpoints. With an increasing number of devices connecting to HDO networks, each endpoint presents a possible entry point from which a malicious actor could launch an attack.
Criminals are sophisticated, but also rely on probability odds. The more endpoints targeted, the higher the likelihood of finding an entry point. A recent review of all medical device disclosures identified a 400 percent increase quarter over quarter, with a prediction that the trend will increase. Whenever an endpoint connects or a user runs software that is unpatched or out of date, the threat surface expands.
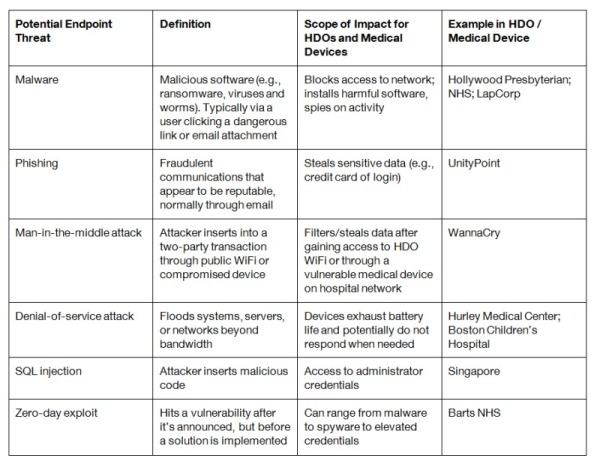
The common phases of hacking (recon, discovery, exploitation, evil, persistence and movement) have identified the biggest threats to endpoints, outlined below:
Endpoint security attacks specifically cost the industry $1.3 billion. What happens once an endpoint has been compromised by one of these methods?
Detect:
A cybersecurity strategy is no small effort and mandates a commitment from people, processes and technology to support. Collaboration between medical device vendors and HDOs to detect if a vulnerability has been exploited are:
● Advanced threat intelligence – self-detecting anomalies and sharing information across all points in real time will minimize the window within which a vulnerability can be exploited
● HDO network segmentation – deviations in traffic movement patterns can be detected and policies executed to identify and isolate the threat before it spreads, which is critical to minimizing the impact of intrusions
● Diligently adopt industry leading practices – beyond having written policies in place, it tactically means being speedy, along with comprehensive coverage of software patching and update processes. Beginning with a robust inventory of devices, relating identified vulnerabilities to potentially compromised devices will allow for prioritized patching by device vendors
Respond:
The medical device vendor and HDO commitment to patient care mandates a level of transparency that must be met when a breach has been identified. Tactical steps to take when made aware of a breach are:
● Communicate with each organization’s breach response team
● Complete forensic analysis in partnership with device manufacturers to determine who/what is responsible
● Contact law enforcement, device vendors and potentially others, considering state and federal requirements
● Engage the public relations team in executing a breach-specific communication strategy
Prevent:
While end-user mistakes have traditionally been marked as the weakest part of a security policy, the trend to fileless attacks is undeniable, as the Ponemon Institute’s 2017 State of Endpoint Security Risk Report stated, 77 percent of endpoint attacks utilized exploits or fileless tactics.
Focusing on endpoint protection means stopping an infection before it has a chance to spread. Assessing the many cyber-risk frameworks available, including the National Institute of Standards and Technology’s Framework for Improving Critical Infrastructure Cybersecurity, key areas of focus specific to healthcare are:
● Prepare a breach response plan! And practice it with all critical stakeholders – including device vendors and HDOs
● Backup and restore – regularly perform backups and restores of data so in the occurrence of an event, there is limited loss of data
● BYOD policy management – determine what is acceptable use, manage device provisioning and monitor devices connecting to the network
● Implement a policy of least privilege, limiting access to only what is required for an end-user to perform their job
No single solution is a silver bullet, and while this isn’t a comprehensive list, a combination of approaches coordinated between medical device vendors and HDOs covering prevention, detection and response is critical to being prepared for the inevitable cyber-attack.
About the author: Mike Kijewski is the CEO of San Diego-based MedCrypt, a medical device cybersecurity company that protects information traveling to and from medical devices with just a few lines of code.
Security is the collective responsibility of all players in a healthcare delivery organization (HDO), from vendors and third parties to threat intelligence-sharing platforms.
What makes healthcare, and particularly hospitals, a popular target?
● Highly valuable data – the volume of personal health information and financial details stored, combined with their sensitive nature, as nearly all of the data is governed by government regulations
● Lack of IT investment and training – healthcare is noted to have the lowest confidence in endpoint security, with 72 percent of participants feeling they are not up to the job of protecting endpoints from exploitation
● Highly connected systems – the scale of the IT infrastructure, overlapping systems, bluetooth/wireless connected devices and data constantly in transit increases the size of the threat landscape
According to the Ponemon Institute, this is the seventh year of healthcare data breaches costing the most, estimated at more than 2.5 times the cost of similar attacks in other industries.
To best defend against increasingly sophisticated cyber threats, we assess the threat landscape of an HDO, typical threats and better practices in preparing for a breach.
Assuming the reality of an HDO includes overlapping systems, lingering legacy systems and connected medical devices, it is easy to conclude HDOs and medical device vendors are faced with securing a complicated array of endpoints. With an increasing number of devices connecting to HDO networks, each endpoint presents a possible entry point from which a malicious actor could launch an attack.
Criminals are sophisticated, but also rely on probability odds. The more endpoints targeted, the higher the likelihood of finding an entry point. A recent review of all medical device disclosures identified a 400 percent increase quarter over quarter, with a prediction that the trend will increase. Whenever an endpoint connects or a user runs software that is unpatched or out of date, the threat surface expands.
The common phases of hacking (recon, discovery, exploitation, evil, persistence and movement) have identified the biggest threats to endpoints, outlined below:
Endpoint security attacks specifically cost the industry $1.3 billion. What happens once an endpoint has been compromised by one of these methods?
Detect:
A cybersecurity strategy is no small effort and mandates a commitment from people, processes and technology to support. Collaboration between medical device vendors and HDOs to detect if a vulnerability has been exploited are:
● Advanced threat intelligence – self-detecting anomalies and sharing information across all points in real time will minimize the window within which a vulnerability can be exploited
● HDO network segmentation – deviations in traffic movement patterns can be detected and policies executed to identify and isolate the threat before it spreads, which is critical to minimizing the impact of intrusions
● Diligently adopt industry leading practices – beyond having written policies in place, it tactically means being speedy, along with comprehensive coverage of software patching and update processes. Beginning with a robust inventory of devices, relating identified vulnerabilities to potentially compromised devices will allow for prioritized patching by device vendors
Respond:
The medical device vendor and HDO commitment to patient care mandates a level of transparency that must be met when a breach has been identified. Tactical steps to take when made aware of a breach are:
● Communicate with each organization’s breach response team
● Complete forensic analysis in partnership with device manufacturers to determine who/what is responsible
● Contact law enforcement, device vendors and potentially others, considering state and federal requirements
● Engage the public relations team in executing a breach-specific communication strategy
Prevent:
While end-user mistakes have traditionally been marked as the weakest part of a security policy, the trend to fileless attacks is undeniable, as the Ponemon Institute’s 2017 State of Endpoint Security Risk Report stated, 77 percent of endpoint attacks utilized exploits or fileless tactics.
Focusing on endpoint protection means stopping an infection before it has a chance to spread. Assessing the many cyber-risk frameworks available, including the National Institute of Standards and Technology’s Framework for Improving Critical Infrastructure Cybersecurity, key areas of focus specific to healthcare are:
● Prepare a breach response plan! And practice it with all critical stakeholders – including device vendors and HDOs
● Backup and restore – regularly perform backups and restores of data so in the occurrence of an event, there is limited loss of data
● BYOD policy management – determine what is acceptable use, manage device provisioning and monitor devices connecting to the network
● Implement a policy of least privilege, limiting access to only what is required for an end-user to perform their job
No single solution is a silver bullet, and while this isn’t a comprehensive list, a combination of approaches coordinated between medical device vendors and HDOs covering prevention, detection and response is critical to being prepared for the inevitable cyber-attack.
About the author: Mike Kijewski is the CEO of San Diego-based MedCrypt, a medical device cybersecurity company that protects information traveling to and from medical devices with just a few lines of code.